VR GATE: Open A Virtual Door to Authenticate Yourself in an Immersive Virtual World

Virtual Meeting Room
Participant #1 is Opening the Virtual Door Using the Hand Controllers.
Participant #2 is Opening the Virtual Door Using the Hand Controllers.
Project Overview
Authenticating Users of VR Applications Through A Simple Door Opening. The Virtual Reality (VR) ecosystem has seen a massive transformation from just a game-playing environment to a point where it is practically applicable in almost every field and supports numerous human activities. Among the innumerable human activities increasingly incorporated in VR are conferences, business meetings, therapeutic appointments, education, shopping, and many more. Such applications must maintain high security and user privacy while not interrupting user activities in the virtual world. Employing the traditional password-based authentication system poses even more vulnerabilities than the many setbacks already shown in the literature since users are fully immersed in the virtual environment. Using second-factor authentication methods such as push-ups and one-time passwords requires users to get out of the virtual environment to finalize authentications, which is not user-friendly. We present an approach for authenticating users in such applications by tracking the position, orientation, and motion behaviors as users perform a simple door opening that leads to the activity, whether a conference, a business meeting, or the like. The focus of our proposed system is to seamlessly validate users without interrupting the user's activity.
Tools
We used the following tools in this Project:
Data Collection
We have designed a virtual meeting room with Unity3D for data collection. We collected data in two sessions with 31 volunteer participants.
Recorded Features
We Recorded the x, y, z and m components of the following (m is the magnitude of x,y and z):
- Position
- Rotation (has no m but w)
- Velocity
- Angular Velocity
- Acceleration
- Angular Acceleration
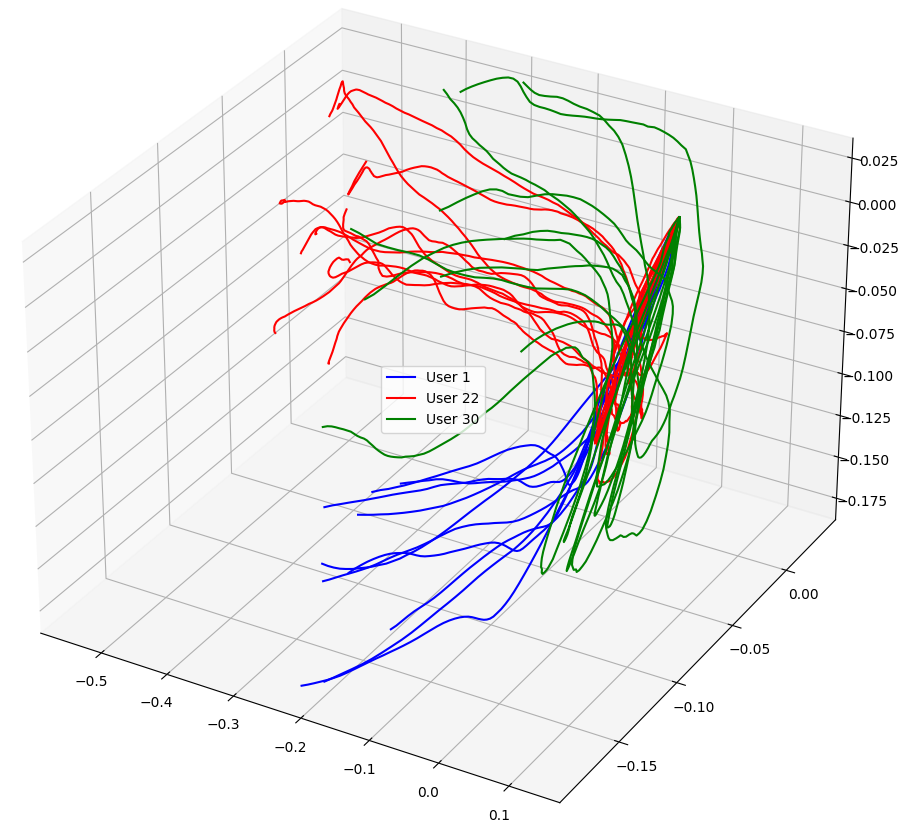
Position Trajectories of Three Users
Methods Used
We used the following machine learning techniques following (m is the magnitude of x,y and z):
- Feature Extraction
- Feature Selection
- Classification with Siamese Network